
How Everyday Devices Are Turning Into Cyber Weapons
Albert Einstein once said, "I know not with what weapons World War III will be fought, but World War IV will be fought with sticks and stones." His words were a reminder of the devastating power of modern warfare and how quickly humanity can revert to primitive survival. While Einstein envisioned a future of destructive nuclear and physical warfare, the recent cyberattacks in Lebanon involving Israel's weaponization of low-tech devices like pagers mark a new, equally terrifying boundary. In this digital era, war is no longer fought solely with tanks, guns, or even nuclear weapons. The battlefield has extended to cyberspace, where even the simplest of everyday objects once considered safe due to their low-tech nature can be manipulated to create serious damage.
This post explores how Israel’s use of pagers to cause mass casualties in the Hezbollah attack marks a dangerous turning point. It highlights the potential for ordinary devices to be secretly hacked and turned into weapons. As we move deeper into the era of cyberwarfare, Einstein's warning about future wars is starting to come true in ways we never expected.
Israel’s cyber forces launched a coordinated attack against Lebanon, targeting critical infrastructure through a sophisticated breach in telecommunications and energy systems. The attack was reported to be made via a Taiwanese company supplying pagers, which rejects (https://www.bbc.com/news/articles/c93yg2w53dzo) all the accusations lately. Allegedly, this operation aimed to disrupt Hezbollah's communications network, but its impact rippled beyond military targets, affecting civilian utilities and financial institutions. By compromising essential digital systems, the attack raised alarm bells across the global cybersecurity community.
Many experts argue that this incident has indeed opened Pandora's box because it reveals just how vulnerable critical sectors such as healthcare, banking, and public infrastructure are to cyberattacks. The attack on Lebanon wasn't just a strike against military communications; it exposed weaknesses in essential systems that keep societies running.
Beyond these possible dangers, the after-effects of these attacks may cause questioning the trustworthiness of so-called ‘low-tech’ devices as these are once considered secure because of their simplicity—are becoming the new frontiers of cyberattacks. Nowhere is this more evident than in the recent attack in Lebanon, where Israel allegedly used pagers, a relic of 1990s communication, to deliver devastating explosions that killed and injured Hezbollah members.
Pagers, long seen as a primitive form of communication, were central to a sophisticated attack on Hezbollah forces in September 2024. By planting small explosives in the batteries of these devices, attackers were able to cause mass injuries and deaths when the pagers were triggered remotely. This method of attack demonstrates that low-tech doesn’t equate to low-threat(L'Orient Today).
Hezbollah, like many organizations, opted for pagers as a "safe" alternative to smartphones, which are easily tracked and hacked. However, this attack revealed that even low-tech devices, when connected to a communications network, can be exploited in ways no one expected. It marked a chilling evolution in how low-tech equipment can be turned into weapons of war(Stanford CIS).

Why Low-Tech Devices Are Vulnerable
Low-tech devices, such as pagers, fax machines, and early mobile phones, have long been viewed as secure because they lack the connectivity and software that make modern devices vulnerable. But as attackers have evolved, they’ve discovered new ways to exploit the very components that make these devices run. The pager attack in Lebanon is just one example of how such devices are being transformed into cybersecurity time bombs.
Here’s why low-tech devices are more vulnerable than you might think:
- Lack of Security: Unlike modern smartphones or computers, low-tech devices do not generally receive software updates or security patches.
- Weak Hardware Security: Many low-tech devices were built in an era when cybersecurity wasn’t a priority. Features like encryption or tamper-proof hardware were not included, as the technology didn’t exist or wasn’t deemed necessary. This makes them highly susceptible to physical tampering, as seen in the pager attack, where components were sabotaged during the manufacturing process (Smartencyclopedia | ENG).
- Outdated Protocols: The communication protocols used by many low-tech devices, such as radio frequencies for pagers, are often poorly encrypted or not encrypted at all.
- Invisibility: Most organizations today focus their cybersecurity efforts on protecting high-tech systems, such as cloud infrastructure, smartphones, and corporate networks. Meanwhile, low-tech devices work under the radar of most security teams, making them easy targets for attackers who understand their potential (Business Today).
The Pager Attack: A Prototype for Future Threats
The pagers, which relied on lithium-ion batteries, were believed to have been compromised during their production or shipment, with tiny explosive devices added to the battery compartment. When triggered remotely by a specific radio frequency, the batteries overheated and exploded, injuring and killing many people including civilians.
This attack is particularly alarming because it targeted what was thought to be a "low-tech" device. Pagers, once a tool of communication in the pre-smartphone era, are still used in certain environments like hospitals and by groups seeking to avoid digital tracking. The attack demonstrated that even the most seemingly trustworthy devices could be weaponized when equipped with vulnerable components like lithium-ion batteries which are widely used because of their high energy density and rechargeable nature. But they also come with natural risks. These batteries can overheat if damaged, short-circuited, or exposed to extreme temperatures. This overheating can lead to thermal runaway, a chain reaction in which the battery’s internal temperature rapidly rises, causing it to ignite or explode (Stanford CIS).
A Template for Future Threats
The pager attack was a display of how low-tech devices can be repurposed for covert military operations. In this instance, the pagers long considered secure because of their simplicity and offline operation were equipped with small explosives during production. These explosive devices were triggered remotely, killing and injuring numerous Hezbollah operatives. What makes this attack so alarming is not just the loss of life, but the method used to infiltrate and exploit the device.(Smartencyclopedia | ENG)
The pagers, originally selected by Hezbollah to avoid the tracking and hacking risks associated with modern smartphones, were thought to be a safe choice. However, attackers exploited the very trust that was placed in these devices by modifying their hardware during the manufacturing or distribution process. The attack showed that no device is too simple to be compromised, and it raised a significant question: If pagers can be weaponized in this way, what about the thousands of connected consumer devices in our homes?
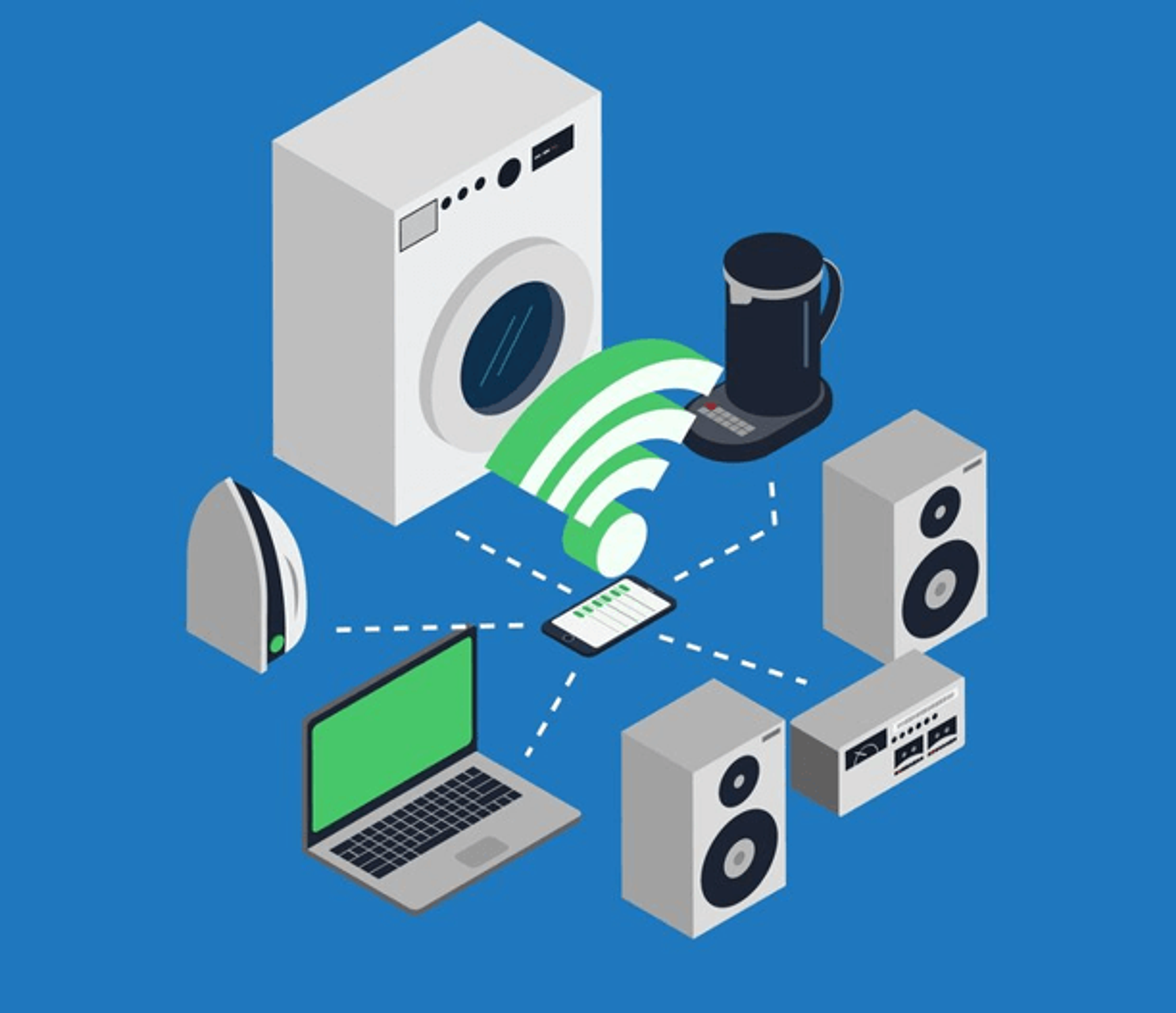
The Rise of Everyday Connected Devices
We live in an era where consumer devices are becoming smarter and more interconnected. From smart refrigerators and voice assistants to wearable health trackers and baby monitors, the Internet of Things (IoT) has created a web of connectivity that spans nearly every aspect of daily life. These devices, designed to make our lives more convenient, often collect and transmit vast amounts of data making them ripe targets for cyberattacks. (Business Today)
However, what many people overlook is that these devices are not just vulnerable to data breaches; they can be exploited physically, much like the pagers in the Hezbollah attack. A smart thermostat, for example, can be tampered with during production to gather data about when a home is occupied. A connected baby monitor could be compromised to spy on families, or worse, to create panic by emitting terrifying noises or false alarms.
How It Could Be Done
Much like the pagers in the 2024 attack, consumer devices can be compromised in various stages of their lifecycle: during manufacturing, in transit, or even post-purchase. Here's how attackers could exploit everyday objects:
1. Supply Chain Manipulation
One of the most insidious methods of infiltration is supply chain manipulation. Attackers could introduce malicious components, such as altered chips or circuit boards, during the manufacturing process. Once these components are integrated into a device, they could enable remote access or control without the consumer ever knowing. This method was likely employed in the pager attack, where explosives were hidden in the devices before they were ever distributed.(Smartencyclopedia | ENG)
In the context of consumer electronics, this could mean that any device — from a toaster to a television — could be compromised before it even reaches the store shelf. Once inside the home, these devices could be used for anything from espionage to physical sabotage.
2. Remote Attacks via Communication Networks
As demonstrated in the pager attack, devices that rely on wireless communication whether radio frequencies, Bluetooth, or Wi-Fi can be vulnerable to remote activation. An attacker could trigger a malicious function within a device using these communication networks. For instance, a smart door lock could be remotely unlocked, or a connected speaker could be used to broadcast false alarms, creating confusion and chaos. (ASIS International)
The Future Threat: Consumer Devices as Tools of Sabotage
While the Hezbollah pager attack was a military operation, the same principles could easily be applied to consumer devices for purposes of sabotage or terrorism. The growing reliance on IoT devices in critical infrastructure adds another layer of risk. As more consumer devices become interconnected, the attack surface expands. The very systems that make life more convenient could be turned into weapons, either for political motives or for profit by cybercriminals.
What Can Be Done?
1. Securing the Supply Chain
By securing the supply chain, companies can reduce the likelihood of malicious hardware or software being introduced into their products.
2. Stronger Encryption and Authentication
Devices that communicate over wireless networks should be equipped with strong encryption and multi-factor authentication to prevent unauthorized access.
3. Consumer Education and Awareness
Understanding the importance of regularly updating firmware, being cautious about the devices consumers bring into their homes, and ensuring that connected devices are properly secured with strong passwords and encryption.

A New Kind of Threat
The Israel-Hezbollah pager attack was a stark reminder that even the simplest technologies can be weaponized in the digital age. But this attack also opened the door to a more frightening realization: our everyday objects the ones we rely on for convenience and security could become tools of exploitation. From compromised supply chains to malicious firmware, the risk of stealth hacking has never been greater.
As we move forward into an increasingly connected world, it is vital that we treat cybersecurity not just as a software issue, but as a hardware issue as well. Every device, no matter how common it is, has the potential to be exploited if we’re not vigilant. The future of cybersecurity depends on recognizing this reality and taking action to protect ourselves from the threats that lurk in the most unexpected places.
TL;DR:
- Israel’s attack on Hezbollah using pagers shows how even simple devices can be weaponized.
- The attack exposed vulnerabilities in civilian infrastructure like telecoms and financial systems.
- Everyday consumer devices, especially IoT, are now at risk of being hacked and used for sabotage or spying.
- Stronger supply chain security, encryption, and consumer awareness are needed to prevent this.
- Cybersecurity must now consider not just software threats but also risks to everyday hardware.
